The biggested misconception?
Dr. Stilianos Vidalis
Disclaimer: I have committed plagiarism to my heart’s content!
“When the power of love overcomes the love for power,
the world will know peace.”
The Beginning…
The evolution of computing
Computer-centric era
Computers have come a long way since the days they were invented. (see Hackers: heroes of the computer evolution). From simple stand-alone batch applications in single-user environments we now have computers able for real-time control, multitasking and distributed processing in true distributed environments. The biggest asset was computer up time. The focus was on physical security. Simple checklists were used for conducting risk assessment. Threat assessment non-existent as threat environments were fixed. The word that best characterises that type of environment is the word ‘static’.

IT-centric Era
The new requirements were user identification/authentication, access control and encryption of COMMS. Security professionals started thinking about a number of new concepts such as: asset, vulnerability, threat, Impact, and likelihood. The biggest asset was definitely COMMS. Unfortunately most assets were (and still are) intangible (see my paper on asset valuation). At the time we had no formal ways to interpret and calculate the threat impact, and the likelihood of threat.

Information-centric Era
The new concepts of the era were E-commerce and generally on-line services. The biggest asset was information. The new requirements were system interrelationships, user behaviours and understanding the system environment. The solutions given at the time to the aforementioned issues were to explore/assess the business, determine controls to implement (instead of implementing everything), promote awareness in trying to minimize expenditure, and assess compliance and control effectiveness in trying to minimise losses.
Knowledge-centric Era
The new concepts of the era are: Knowledge extraction, virtualisation and virtualised environments, and social networking. The biggest asset is considered to be ‘knowledge’. The threat assessor is called to understand system behaviour, and user and vulnerability interrelationships. Security countermeasures had to evolve once, from protecting infrastructures to protecting information, and then they had to evolve again, into protecting knowledge… We leave in a knowledge-based socially-driven computing era where we take everything for granted and we never bother in developing our own critical opinion. Instead we plagiarise opinions. It is easier…
The one thing that has really changed amongst the aforementioned eras is the speed at which we exchange information.
What is information?
Information encapsulates a wide range of concepts and phenomena. They relate to both processes and material states which are closely inter-related… Information can be a product, which encompasses information as thing, as object, as resource, as commodity, or what is carried in a channel, including the channel itself, or even the actual contents of a medium. Information has a number of different abstractions:
Data can be individual observations and low level primitive messages. We use tools to collect data from a number of diverse sources that we then try to organise.
Information is the sorted, classified or indexed data into organised sets. Information is a great commodity that is usually exchanged between human operators that thrive to acquire enough as to develop knowledge about the issue at hand.
Knowledge: Understanding of information provides a degree of comprehension of both the static and dynamic relationships of the objects of data and the ability to model structure and past (and future) behaviour of those objects. Knowledge includes both static content and dynamic processes.
Expertise is the combination of knowledge on a specific topic, item, process
Knowledge is extremely important. Knowledge will allow you to achieve an information superiority state over your adversaries. “Information superiority is the capability to collect, process, and disseminate an uninterrupted flow of information while exploiting or denying an adversary’s ability to do the same.” As we leave in a socially-driven knowledge-based computing era, expertise will allow a person or a group of people to swiftly take advantage of their information superiority status. As our ability to collect and process information became better and faster, so did the ability for committing crimes, based on our easily acquired expertise.
What is crime?
A crime is an act that violates the basic values and beliefs of society. Those values and beliefs are manifested as laws that society agrees upon. However, there are two types of laws. The natural laws are rooted in core values shared by many cultures. Natural laws protect against harm to persons (e.g. murder, rape, assault) or property (theft, larceny, robbery), and form the basis of common law systems. Then there are statutes that are enacted by legislatures and reflect current cultural mores, albeit that some laws may be controversial. Marxist Criminology, Conflict Criminology and Critical Criminology claim that most relationships between State and citizen are non-consensual and, as such, criminal law is not necessarily representative of public beliefs and wishes, rather it is exercised in the interests of the ruling or dominant class.
Criminology is the scientific study of the nature, extent, causes, and control of criminal behaviour in both the individual and in society. It’s an interdisciplinary field in the behavioural sciences, drawing especially upon the research of sociologists and psychologists, as well as on writings in law. Areas of research in criminology include the incidence, forms, causes and consequences of crime, as well as social and governmental regulations and reaction to crime. These will be the areas that we will analyse in this report in our attempt to understand ‘ethical hacking’. For studying the distribution and causes of crime, criminology mainly relies upon quantitative methods, but in our case we will base our arguments on qualitative methods.
The way in which crime is defined is dynamic and reflects each society’s immediate needs and changing attitudes towards the local varieties of conduct. The process depends on the values underpinning the society, the mechanisms for resolving political conflict, the control over the discourse, and the exercise of power. Capitalist states are often reluctant to pass laws to regulate large corporations, because this might threaten profitability, and that these states often use considerable sums to attract regional or national inward investment from large corporations. They offer new investors: preferential tax concessions not available to the ordinary citizen or local business if foreign investment is sought; loans, guarantees and other financial support on preferential terms; directly targeted grants and other subsidies; and a purpose-built infrastructure to subsidise the set-up costs.
Who is the criminal in the aforementioned scenario? Who is the biggest and worse threat agent to society? Who is able to operate outside the law without any consequences what so ever? We will come back to these questions in the following parts of this report.
What is a criminal?
For a complete analysis of threat agents see my paper on threat agents and their attributes.
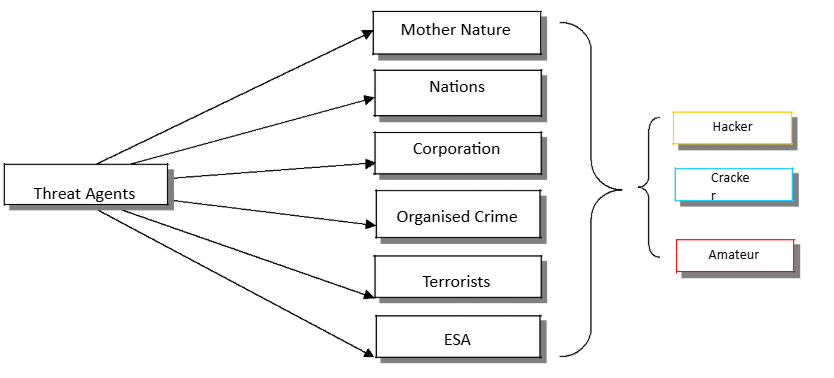
Amateur
is a huge knowledge depot. A lot of hacking tools and “hacking-related” information can be found in the public domain, and is readily available to anyone with a computer. Amateurs have minimal knowledge of the art of computing and “hacking”, they use of-the-self ambiguous “hacking-called” tools. They can cause no real damage expect increased network traffic. Usually (unless employed) they are motivated by their need to “show-off”
Hacker
Anyone who is interested in the way things are working, anyone who is trying to analyse what is going on behind the scenes, and anyone who is not happy with whatever is on the surface. Most hackers use sophisticated tools and have the knowledge to cause damage but hackers do not break the law as they do have cyber-ethics and know what is and what is not legal. They are usually motivated by their need to acquire knowledge
Cracker
Crackers can be seen as “evil” hackers. They are aware of their power and they like abusing it. The bigger their target, the more resources they will allocate in cracking it. They are motivated by their
need to crack as many computer systems as they can, cause as much damage as they can, bring community operations to a standstill, and leave their signature behind.
Threat Agents can employ hackers, crackers and amateurs to achieve their goals. Hackers, crackers, and amateurs can be part of threat agent groups. We can think of this as a two-way inheritance. Each combination has different attributes, and more than one combination can exist in any one group.
Career Path of a Cyber-Criminal
Kiddiots / Script Kiddies: Lowest level of cyber-criminal. Finds code published on the internet and changes it slightly to launch a new variant of a virus.
Virus Writer: Has gained more code writing skills. Creates virus code in spare time and either publishes it on the internet or launches an attack via email.
Spare Time “Cyber-Criminal”: The thrill of virus writing has given way to greater risk taking. The virus writer has now become entrenched in the cyber-criminal world. However, still holds down a regular job. A number of spare time cyber-criminals have jobs in the IT industry.
Professional “Cyber-Criminal”: Full time cyber-criminal who makes his money from stealing credit card information of victims or cracking into bank websites and either stealing money or blackmailing the bank.
Phisher: More complex skill set than a professional cyber-criminal. Creates websites that look like, for example, a high street bank. He then steals account passwords when users enter them thinking that they are in their usual site.
Cyber Criminal for Hire: New breed of cyber-criminal that hires out his skills to organised criminals for the highest price.
Computer VS Crime
Defining computer related crime
The computer can be used in three different ways in order to assist a crime. It can be used as the ‘tool’ that the criminal uses for performing the crime. It can be the ‘target’ that the criminal manages to attack and penetrate. It can also be the ‘storage area’ that the criminal can use in order to save information related to his crimes.
A computer is defined as an electronic, magnetic, optical, electrochemical or other high speed data processing device performing logical, arithmetic, or storage functions, and includes any data storage facility or communications facility directly related to or operating with conjunction of such device.
Defining computer related crime is not as straight forward as defining a computer though. Computer crime is/are the “computer-mediated activities which are either illegal or considered illicit by certain parties which can be conducted through global electronic networks” (Thomas and Loader 2000:3).
The United Nations Manual on the Prevention and Control of Computer Related Crime states that cybercrime “can involve criminal activities that are traditional in nature, such as theft, fraud, forgery and mischief, all of which are generally subject everywhere to criminal sanctions.” Another resource was stating that an act of cybercrime is any act which relies significantly or entirely on the use of one or more computers and gives rise to a result that is, or has a traditional counterpart that would be, subject to criminal sanction. I particularly like the last definition as it gives me (as an investigator) a clear link to something that I can understand, the Judge can understand and the Jury can relate to, the concept of traditional crime.
Over the years, and after a lot of time brainstorming, discussing, arguing and working behind closed doors I have come up with the following classification that helps me not only to relate to, but also to link crime to specific assets.
Computer Crime is defined as the activities that target data and/or low level data operations using computers as the means for conducting those activities
Cyber Crime is defined as the activities that target information and/or knowledge or the high level data operations that manage information and/or knowledge of legal bodies, including software programs, using computers as the means for conducting those activities.
E-Crime or economic crime is defined as those computer crime or cyber-crime activities where the main purpose of the criminal is financial gain.
Naturally when you talk about crime you also have to talk about evidence. Evidence can be defined as items that can be used to assist a party or parties in either proving or disproving the fact of a matter and allow the burden of proof to be reached. ‘Evidence’ has the following attributes:
Authenticity, the evidence can be related with the events of the incident;
Demonstrational, they can be presented in a form that can be submitted to the court;
Best Evidentially, they represent the evidence in the more complete form;
Probative, the information can be presented practically
Real Evidence is an object that is involved in a case or may have played a role in the action in question. The object may also be able to be examined by a Court or an expert witness who is suitably qualified to provide guidance to the Court regarding the item. Hearsay Evidence is less common, however, is information given to a Court by someone who is not a direct witness of an event or action and, therefore, does not have first-hand knowledge of something but has heard it from another source. Testimonial Evidence is provided by a witness. This may be a witness to the alleged offence itself or a professional witness who has examined the item of real evidence and are providing findings based on that examination. Circumstantial Evidence can be used to draw an inference of guilt sufficiently to prove a case beyond reasonable doubt; however, it is not drawn from fact and can be open to interpretation. Direct Evidence comprises of evidence of the allegation itself and if that evidence is accepted then the allegation itself will be proven.
The changing face of computer crime
In the early days of computers, ‘computer crime’ meant breaking into, or stealing, a single PC. Today, the term spans a wide range of fast-evolving offences. Broadly speaking, cybercrime can be divided into two categories.
Cyber-Crime: Old
Computer and telecommunications systems are used to attack legal interests protected by criminal law, through activities such as extortion and fraud. Cybercrime has developed from geeks in their bedrooms to more organised criminal gangs, and now organised crime is harnessing the internet with new systematic and professional ways to commit illegal acts such as: growth of new technologies such as automated ‘bot-nets’ operating in virtualised environments and cyber terrorism. Professor Ulrich Sieber of the Max-Planck-Institute for Foreign and International Criminal Law in Freiburg, Germany, says that “cybercrime represents the fastest-growing category of crime in Europe.” Britain, Holland, France, Germany, Italy and Spain have long since been identified as favourite targets for cyber criminals. Cybercrime is mirroring traditional offline criminal activity, with an estimated 70% of malware written purely for profit.
Cyber-Crime: New
Of course we also have a new breed of crime, those offences against the confidentiality, integrity and availability of digital information and computer infrastructures. Cracking is the best documented form, but more recent developments include parasitic computing, whereby criminals use a series of remote computers to perform operations, including storing illegal data such as pornographic pictures or pirated software.
The impact
The levels of impact of computer-related crime vary, with the Internet providing the playground.
The internet as a vehicle of communication- sustaining existing patterns of criminal behaviour e.g. drug trafficking, stalking, hate speech etc.
Internet creates a transnational environment- new opportunities for harmful activity that are subject to existing criminal law e.g. fraud, paedophile activity.
Internet transgresses time and space- creating new harmful activities e.g. Appropriation of illegal downloads.
For a complete analysis do consult the ‘Breach Reports’. ‘Lone’ cyber criminals – crackers, script kiddies, kiddiots, and lamers – committed the bulk of the reported computer related crimes until now. For these individuals, publicity and notoriety were always the main motivation. “They” are stereotypically young, male and socially on the fringe. As John Suler, expert on the psychology of cyberspace at Rider University, Lawrenceville, NJ, explains:
“Some are captivated by the challenge and excitement of venturing into forbidden territories. They derive a sense of accomplishment, mastery, and power from doing what others can’t. Impressing other users, especially one’s fellow ‘hackers’(?), is a source of self-esteem. Cracking the system of the ‘institution’ reflects a defiant attitude towards authority figures”.
“A hacker feels pressured to demonstrate that they are better and smarter than anyone. The cat-and-mouse drama of beating the system becomes a tireless, relentless quest to prove oneself.”
Malicious viruses, the odd email swindle or pyramid scheme have always been a tiresome feature of the internet. They have usually been the work of some backroom scam artist or anarchic individual out to get attention by cracking a system. In the last two decades cybercrime has become less open to ‘ordinary’ criminals as criminal organisations have started to realise the potentially huge financial gains to be made from the internet. Organised crime has been quick to adapt to the new hi-tech world, replacing knuckledusters and baseball bats with sophisticated invisible weapons such as bot-nets. Traditional crime gangs are starting to use the internet not only for communication but also as a tool to commit ‘classic’ crimes – such as extortion, fraud, money laundering, intimidation and theft – more efficiently and with less risk, and to move into new fields of crime.
Due to the internet’s global reach, the temptation is highly attractive – and the scale of the problem is massive. The growth of e-business and internet usage as part of everyday business has made it easier for organised crime gangs to facilitate and cover up their criminal activities. Money can be moved very rapidly, with only a couple of clicks of a mouse; and it is difficult for police to monitor and follow the financial transactions of international criminal gangs. The creation of ‘virtual identities’ gives a greater anonymity to the activities of organised criminals. Computer and printer technology makes it easier to produce forged documents of higher quality so they are more difficult to identify. A report produced back in 2005 for the Octopus Programme (EU Project) identified four European countries where traditional organised crime is already going online: Denmark, Portugal, Romania and the UK. There are a lot of well documented cases where the new nature of the beast is apparent.
Criminal Gangs are using young “cyber-criminals” to make money. Criminal organisations are ‘buying’ thrill-seeking ‘black-hats’ and ‘script kiddies’ to provide the expertise and tools they need to commit ‘classic’ crimes – such as protection rackets – online. It is a form of modern child labour, similar to the classic hierarchy of drug dealer and drug runner, with ruthless bosses and a strict pecking order, where members in the lower ranks – like teenage script kiddies – are forced to take bigger risks, are expendable and will be cut loose to protect their masters. Scotland Yard have already had reports of criminals who have approached script kiddies through internet chat rooms. A spokesman said: “We have seen intelligence to suggest that European organised crime is hiring hackers to carry out computer attacks.” The use of script kiddies can be seen as a new form of child labour, in the same way as a drug dealer uses a 13-year-old child as a runner. These script kiddies do
not have an overview of the whole context of an organised crime operation and can easily be dumped at the end. This kind of activity has expanded to the whole of Europe. Organised Criminals are also profiting from the Internet.
Protection rackets
In the old world shopkeepers were forced to pay a ransom to organised criminal gangs to stop their shops being robbed or set on fire. Today organised criminals try to force e-businesses to pay a ransom to ‘protect’ online shops from online attacks.
Bank robbery
Old-fashioned bank robbery: gangs rob high street banks / security vans. Today they crack into a bank’s computer systems and transfer money over electronic payment systems. Today criminals steal credit card statements and utility bills from rubbish bins to fraudulently use the identity of their victims. If they do not want to walk amongst garbage they use technology and install a keyboard sniffer programme on their victim’s computers that collects user names and passwords and sends them back to them for fraudulent use.
Teenage drug runners
In the past, organised drug dealers were using young kids to deliver money, guns and drugs between gangs and customers. Today organised criminals are using script kiddies and young crackers to deliver and launch web-based weapons in online protection rackets and hacking scams.
ID Thiefs
Today criminals phone up their victims and ask for their credit card number, security details or passwords, pretending they are from the security department of a bank. Alternatively they send phishing emails, directing the victim to the website of a criminal that mimics the bank’s website, asks for a credit card number, pin numbers and security details, and stores them for the criminal’s own use. If they are bold enough they knock at the front door and pretend to be from a legitimate business. In the meantime, their accomplice enters through the back door to steal valuable possessions.
Malware
Of course the same mechanism works online. The ‘back door’ on a PC is opened up through illegal hacker behaviour, enabling viruses to spread easily and infect a machine.
Levels & types of computer crime
Computer crime appears to be relatively easy to commit. As a result, the internet may also change the characteristics of offenders. In the real world, legal businessmen engage in organised forms of economic crime. The opportunities offered by the internet may tempt legal commercial entities to organise for computer crime – that is, become organised computer criminals. Dr Ernst-Heinrich Ahlf at the BKA also identifies an increasing threat of computer attacks coming from within companies: “According to a recent survey, 52% of the attackers are employees or working in the same industry, so they have the same skills and knowledge as IT and security experts.”
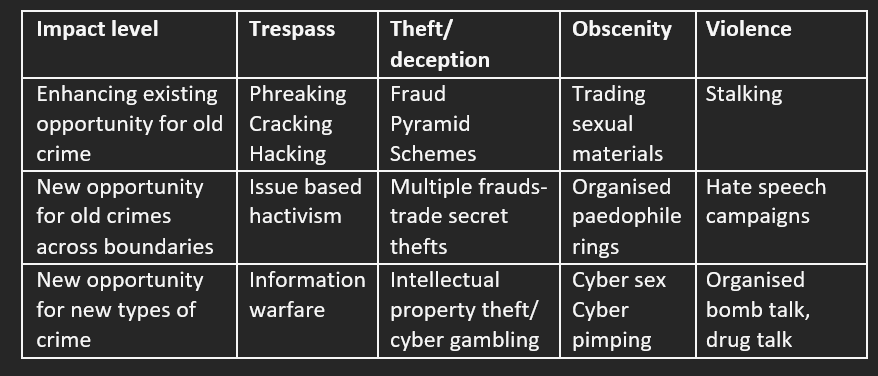
The Matrix: levels and types of computer crime
Challenges to policing cybercrime
Volume
Jurisdiction
Under- reporting
Police culture
Limited recourses
Things to remember
Criminals do not need to be physically present at the scene to commit the crime.
Computer crimes can be committed across geographies i.e. someone in Russia could commit a crime in the UK / France / Germany / Italy / Spain etc.
Using computers, the crime is carried out automatically, at high speed and attacks a vast number of victims at the same time, making it harder to track and prosecute.
It is extremely challenging to police computer crime using the traditional mechanisms.
Criminal Profiling
The Science?
Criminal Profiling is used to analyse the background, possible interests, and characterisation of suspects believed to be responsible for committing a crime. Profiling according to Ainsworth, (2001) ‘generally refers to the process of using all the available information about a crime, a crime scene and a victim, in order to compose a profile of the (as yet) unknown perpetrator. Law Enforcement agencies often seek help from psychologists, criminologists, psychiatrists and other professionals that specialise in human behaviour when trying to catch a suspect. Holmes and Holmes, (1996: 156) put forward the idea that profiling has three aims which attempt to provide the Criminal Justice System with information, specifically;
a social and psychological assessment of the offender;
a psychological evaluation of possessions found with suspected offenders;
consultation with law enforcement officials on the strategies which might best be employed when interviewing suspects. (Cited in Ainsworth, 2001, p 15)
Criminal profiling has been used by the United States Federal Bureau of Investigation since the 1970’s when it was recognised as an official field and has championed its use in past analysis. There is a difference of opinion on the most effective profiling process, but real world instances have proved that criminal profiling can be helpful and lead to accurate arrests. However, when used alone, profiling can prove potentially dangerous and is completely useless. It must be used as a combination of detailed case analysis, accurate information and reliable records and statistics to prove it’s true worth. (Nykodym, et al, 2005)
Offender profiling is a criminal investigative tool that makes conclusions about the characteristics of a likely offender based on the behaviour exhibited at a crime scene or if there is more than one crime scene, the series of crime scenes. Canter and Alison (1997) point out ‘that the most controlled information is that gathered from the actual crime scene: “Evidence of this nature tends to be physical, such as DNA testing, ballistics and fingerprinting.” (Evans, 1996, cited in Alison, 2005, p 11) In a manual called Crime Classification Manual which is used for offender profiling issued by the FBI, Douglas et al., (1992: 21) explain that: “The crime scene is presumed to reflect the murderer’s behaviour and personality in much the same way as furnishings reveal the homeowner’s character” (Cited in Alison, 2005, p 3)
The type of profiling most used by the FBI, is retrospective profiling (explained later). This approach uses any evidence left behind by a criminal to develop a likely description of that person. “The idea is to link a specific person or persons to a specific crime (or series of crimes) that have already occurred based on personality and behavioural characteristics that have been identified through analysis of the crime scene and the facts of the case” (Nykodym, et al, 2005). So in studying the crime scene, profilers can in fact come up with a viable description of the likely perpetrator.
Profiling is not conclusive about the individual, but depends on probabilities to create a combination of the likely traits of the individual who committed the crime. It functions as any other piece of
forensic evidence in an investigation, operating to narrow the search parameters of law enforcement authorities. Law enforcement authorities, recognize that it is an important but limited tool that is used in conjunction with other forensic evidence to help discover the identity of a perpetrator. Accurate profiling requires a careful compilation of theories and hypothesis from psychology and sociology as well as data obtained by examining evidence and methods of operation employed by criminals in previous crimes.
Nowadays, profiling takes two approaches; prospective and retrospective. Prospective profiling endeavours to create a “template” of a particular offender, i.e a serial murderer or a child molester based on the characteristics of previous offenders. These prospective profiles are then held over a specific population in order to narrow down and predict who will commit these types of offences. This approach is heavily criticised because it is often overly inclusive and can lead to false allegations. Retrospective profiling is the opposite of prospective profiling and is mostly used by the FBI. This approach is after the facts and case specific. It uses the clues left behind by an offender to develop a description of that person with the idea of linking the person or person’s to a crime scene or scene’s that have already occurred based on personality and behavioural characteristics that have been identified through analysis of the crime scene and the facts of the case.
We will briefly discuss a couple of profiling methodologies in order to understand how to put together a profile for a ‘hacker’.
The Methodologies
FBI Crime Scene Analysis
The FBI model has developed into Crime Scene Analysis, and incorporates six steps;
profiling inputs;
decision process models;
crime assessment;
criminal profile;
the investigation and
apprehension. (Douglas et al,. 1988; Cited in Rogers, 2003)
The basis for the analysis is still the offender dichotomy of being organised or disorganised. By exploring the crime scene the investigator tries to identify appropriate evidence to pin point an offender modus operandi or any signature behaviours. This will then highlight whether the offender is organised or disorganised but each category shares common characteristics that the investigator can use to narrow down the number of potential suspects and assist in developing an interview strategy.
Investigative Psychology
Another approach is Investigative Psychology (IP), developed by Canter. It is similar to the FBI model as it also heavily relies on statistics obtained from offender databases. (Canter, 1995) IP uses five factor models which include:
interpersonal coherence,
significance of time and place,
criminal characteristics,
criminal career and
forensic awareness.
Behavioural Evidence Analysis
Behavioural Evidence Analysis (BEA) is based on deductive logic and was developed by Brent E Turvey. It is more reliable to look at the forensic evidence and then use the criminal event to reconstruct the behaviour. The BEA approach has four steps and two primary phases:
the investigative phase which occurs when a crime has happened, but no offender caught for it
the second phase deals with addressing a known event with a known offender, (i.e. there is a suspect).
The first step the ‘equivocal forensic analysis’ is to collect as much evidence as possible. Step two involves a detailed, in-depth analysis of the victim, who Turvey argues, should be profiled and analysed as much as the offender. The why, how, where, when and who of the victim relates directly to the offender (Turvey, 1999). The third step the ‘crime scene characteristics is where the focus is on unique, distinguishing features of the scene that are correlated with the offenders’ behavioural decisions (Turvey, 1999). The fourth step ‘offender characteristics’ combines what has been collected in the other steps which results in a determination of the offenders probable behavioural and personality characteristics.
Things to remember
Criminal Profiling is an important tool to help with the investigation of crime and criminal behaviour. In order to carry out a successful investigation, the profiler needs to be eclectic in Criminology, Sociology, Psychology and also geographical aspects. The theories looked at in this section both seem to believe that people who turn to crime are born with a gene to make them commit crime or that they learn how to be criminals by others including our peers. However, if this were true then all people who carried the criminal gene would be able to be pin pointed at birth thereby allowing law enforcement agencies to track and control them before them have the chance to commit crime.
Everyone is exposed to criminal behaviour at some point in their lives, be it by a personal encounter or through watching others or the television, so if the learning theory was true for everyone, then everyone would therefore be committing crimes. Not all criminals though fall neatly into this package.
The mapping of crimes only gives an indication of criminal activity if the crime has been reported before. It is of no use unless it has been reported or recorded. An understanding of the influence of the environment on a particular crime would be useful in predicting criminal behaviour. This would then enable profilers to know why particular crimes are committed by someone in a particular location at a particular time.
Computer Criminal Profile
Profiling problems
It is impossible to build the right profile for each and every cybercrime, much like conventional crime, because each cybercrime is committed under different circumstances and different motives may be at the centre of the crime. The motives and the circumstances should always be considered when a profile is constructed. When studying the common attributes of a computer criminal it has been suggested that like “real” criminals, cyber-criminals usually need to justify their actions to themselves and they do so by thinking that the laws cause harm to themselves. Computer criminals often feel that some parts of the law deserve to be independently tested for effectiveness of their team work and validity of their actions. Some even feel that because of their position, intelligence or skill set, they are above the law and can do what they see fit because of their situation. Others feel that they are untraceable therefore not punishable. There are certain general characteristics of a cyber-criminal to look out for which include an active imagination, manipulative and risk-taking nature, a substantial amount of technical knowledge and contempt for the law or feeling above the law. There are also certain motivations that cyber-criminals will possess which can range from least harmful to very harmful motives. Take for example the desire for entertainment, this usually applies to youngsters who have been introduced to “hacking” for the very first time and so experiment to try out various methods of hacking to see what works and what does not. Another possible motive could be profit. This is the most widespread motive behind all cybercrimes.
A usable template?
My background is on threat assessment so I will follow my methodology for attempting to understand the ‘Hacker’ by examining attributes such as:
Motivation
Capability
Knowledge o Resources
Motivation
The concise oxford dictionary defines the word motivation as meaning: “Supply a motive to cause a person to act in a particular way.” In the context of a threat, motivation is considered to be identification of both the reasons why someone would launch an attack and a measure of the degree to which the attack would be pressed home. The factors that motivate a computer criminal are diverse and might operate singly or in unison:
Political – discussed later
Secular – supporting secular believes will motivate the criminals to a high level of action,
Personal Gain – it can be financial gain, acquisition of knowledge, and/or peer recognition. Hackers will be highly motivated when they are hunting for knowledge, crackers will be highly motivated when they are trying to be recognized, and organized criminal groups will be highly motivated when there is a financial gain behind their actions.
Religion – This is one of the most regularly observed motivational factors. “Holy” wars have been fought throughout history. While the traditional wars are mutating to become informational wars, this motivational factor is expected to become one of the most
important ones. People are ready to die to fulfill their religious belief and will proceed to extreme actions for doing so. Attacks caused by this motivational factor are expected to be conclusive.
Terrorism – Cyber-terrorism is the next mutation of terrorism, as we know it in the 21st century. Although most recognized terrorist groups do not have the capability to enter such a phase, there is more than one instance of such groups displaying cyber-terrorist actions. Traditional terrorist actions have the unique goal of causing terror. Cyber-terrorist actions will have exactly the same goal, so the attacks will have quite a large impact on the enterprise.
Curiosity – Crackers’ and hackers’ main line of defence. A hacker moved by curiosity is expected to go in an extreme way in order to fulfil this basic need. Attacks initiated by this factor are expected to succeed as time becomes of no importance. An agent will not spend extreme resources, but it will try a variety of methods in order to acquire the necessary information.
Kiddiot Profile
In today’s interconnected world, the WWW is a huge knowledge base. There are a lot of tools (Barber ’01) and “hacking-related” information in the public domain, readily available to anyone with a computer attached to the Internet. One can go to a shop and buy books that explain techniques that were used in the past. “Hacking” & “cracking” is seen by the majority of people as some sort of magic. It is very popular amongst the younger generation. They have minimal knowledge of the art of computing and the art of “hacking”, they use off-the-self ambiguous “security” tools, which are downloaded from the Internet, and can cause no real damage to reasonably protected systems except increased network traffic. Their motivation is to “show-off” and gain peer acknowledgement. Theoretical knowledge does not convert an individual into a hacker. Having a set of tools installed in a PC, and having the knowledge in using those tools does not make one into a hacker. Having a Degree in information security does not make one into a hacker.
Hacker Profile
“Any hacker who’s motivations become malicious or criminal, becomes a cracker” (Barber ’01). Most hackers will never admit outside their environment in being hackers. Many organizations are surprised to find they have hackers on the payroll (Kovacich ’00). A hacker is interested in knowledge and not in destruction. A hacker believes that hacking is an intellectual thrill. In an attempt to extend the definition of the hacker I will say that a hacker is not only someone dealing with computers, but also someone who is interested in the way things are working, someone who is trying to analyze what is going on behind the scenes, and someone who is not happy with whatever is on the surface. Hackers are not socially inept. The sophistication with which hackers manage to “acquire” information shows an ability to relate to the social world (Hoath ’98). Most of the time hackers are very pleasant individuals as long as they are not amongst their peers. It is observed that once two hackers “recognize” each other for what they are, there will go through a “ceremony” of “showing teeth and claws” in order to understand each other’s “capabilities”.
A hacker does not consider that what he does is bad, evil or illegal. A hacker sometimes does not want to realize that what he does is bad, evil or illegal. Most hackers have a very good knowledge on one of the many aspects of computers. Most hackers use sophisticated tools and have the
knowledge to cause real havoc to a computer system (see (Hoath ’98). Fortunately, most hackers do not normally abuse their power unless they are prompted, but once they do, once they break the law then as far as I am concerned they become crackers and there is no way back. For justifying that I will use an example from the world of martial arts. Martial artists have developed great skills in using their extremities as weapons but I still have to meet one that will willingly use his skills amongst the public. In paraphrasing Hollywood… with great skill comes great responsibility…
Hackers can have a range of different “experience levels”. Their motivation is always and forever to acquire knowledge. The modern world divides them in “black hats”, “grey hats” and “white hats”. There are certainly other types of hats as well. I particularly like red hats as I am supporting Olympiakos in football…
According to the hype the “black hats” are breaking the law and the “white hats” are making their “experiments” in isolated environments without breaking any laws, intentionally or unintentionally? Apparently this last category can be a great asset to an organization employing a number of these individuals working as security experts, testing their systems against potential threats (Rees ’96). Of course these individuals will have to have the ethical background in order to be able to differentiate between legal and illegal actions.
A hacker can be seen as the modern secret service agent (?), operating in a huge battle theater, the cyberspace. In the same way that MI5 agents do not break the law during their operations, hackers only go about practicing their art. You are not breaking the law when you have permission to perform your operation, do you? We will be discussing this very topic in the following section.
Cracker Profile
In my mind Crackers can be seen as the “evil” hackers. They are aware of their power and they enjoy abusing it. They are not interesting in just acquiring knowledge, but also using that knowledge in order to cause havoc to legitimate computer users and corporate networks. The bigger the goal, the more resources they will allocate in achieving it. Their motivation is to hack and crack as many computer systems as they can, cause as much damage as they can, bring computer operations to a standstill, and leave their signature behind. That is also their weakness as in their pursue for power they need to let people know who they are.
Democracy & Civil Rights VS Information Security
Forms of Government
Monarchy – rule by one
Oligarchy – rule by minority
Republic – rule by law
Democracy – rule by majority
Anarchism – rule by all (any one person may step up)
Chaos – rule by no one
According to a bam called Plato that lived just outside the Athenian market under the Acropolis the third worst regime is oligarchy, the rule of a small band of rich people, millionaires that only respect money. Then comes the democratic form of government, which is susceptible to being ruled by unfit demagogues. Finally the worst regime is monarchy, where the desires of the ruler become law and there is no check upon arbitrariness. Today we say that the western world is civilised because it is democratic?
So: democracy = civilisation?
Democracy
Democracy is a form of government in which power is held directly or indirectly by citizens under a free electoral system. Δημοκρατία = δήμος + κράτος. I should know about this, no? It started in in Athens in 508BC (I blame the bloody Athenians for the mess our world is into nowadays).
Basic Democratic Principles
All members of the society (citizens) have equal access to power
All members (citizens) enjoy universally recognized freedoms and liberties
Above principles derived from the political philosophy of Democracy (and Wikipedia…)
Political Philosophy
Political philosophy is the study of the city (polis), government, politics, liberty, justice, property, rights, law and the enforcement of a legal code by authority:
what they are, why (or even if) they are needed,
what makes a government legitimate,
what rights and freedoms it should protect and why,
what form it should take and why,
what the law is, and what duties citizens owe to a legitimate government, if any, and
when it may be legitimately overthrown—if ever.
Polis
A polis is a city, a city-state and also citizenship and body of citizens. The term city-state which originated in English does not fully translate the Greek term. The poleis were not like other primordial ancient city-states which were ruled by a king or a small oligarchy, but rather a political entity ruled by its body of citizens.
The polis of Sparta for example was established in a network of villages. The term polis which in archaic Greece meant city, changed with the development of the governance center in the city to indicate state (which included its surrounding villages), and finally with the emergence of a citizenship notion between the land owners it came to describe the entire body of citizens.
The ancient Greeks didn’t refer to Athens, Sparta, Thebes and other poleis as such; they rather spoke of the Athenians, Lacedaemonians, Thebans and so on. The body of citizens came to be the most important meaning of the term polis in ancient Greece.
Justice according to Plato
Justice is the action of doing what one ought to do, or of doing what one does best, according to one’s class within society. A just society is one in which the organization of the polis, mirrors the organization of the tripartite soul. Thus the three classes in the polis each correspond to a part of the soul, as the guardians correspond to the rational part of the soul, the auxiliaries correspond to the spirited part of the soul, and the working-class corresponds to the appetitive part of the soul. The guardians must be wise, the auxiliaries must be courageous, and all three (including the working-class) must exhibit good-sense and practicality.
Defining Justice (A)
…initial definition: Returning debts owed, helping friends while harming enemies. Socrates though (another bam that had decided to be a student for life instead of getting a real job) claims that the just man would never do harm to anybody. The rest of bam crew attack Socrates by saying that justice is what is good for those in power over the polis…
Defining Justice (B)
The rulers are the source of justice in every city, and their laws are just by this definition since, presumably, they enact those laws to benefit themselves and the Polis (they are members of the polis). Socrates then asks whether the ruler who makes a mistake by making a law that lessens their well-being, is still a ruler according to that definition. (Does it seem that I was actually there?) They argue that no true ruler would make such an error. This agreement allows Socrates to undermine the definition of justice by comparing rulers to people of various professions.
Apparently he argued that an artist is someone who does his job well, and is a knower of some art, which allows him to complete the job well. Rulers who enact a law that does not benefit them firstly, are in the precise sense not rulers. (lol… I ‘ve lost myself there… but if you read the above statement again and think about the reverse statement then it makes sense, no?) So the strong man who makes a mistake is not the strong man in the precise sense, and that some type of knowledge is required to rule perfectly?
Defining Justice (C)
The just as well as the unjust man would do the same if they had the power to get away with injustice exempt from punishment. The only reason that men are just and praise justice is out of fear of being punished for injustice? The law is a product of compromise between individuals who agree not to do injustice to others if others will not do injustice to them. If people had the power to do
injustice without fear of punishment, they would not enter into such an agreement. So, is the just life better than the unjust life?
Can we possibly say that justice is the concept of moral rightness based on ethics, rationality, law, natural law, fairness and equity?
Socrates Conclusion on Justice
Ultimately Socrates constructs a city in which there is no private property, no private wife and children, and no philosophy for the lower castes. All is sacrificed to the common good and doing what is best fitting to your nature. Socrates never positively stated what justice is. His solution was to make justice not relevant by creating a city where justice is lost, not even needed, since the perfect ordering of the community satisfies the needs of justice in human races’ less well ordered cities
Socrates perfect Polis
The “good city” is depicted as being governed by philosopher-kings; disinterested persons who rule not for their personal enjoyment but for the good of the city-state (polis). The paradigmatic society is hierarchical, but social classes have a marginal permeability; there are no slaves, no discrimination between men and women. In addition to the ruling class of guardians (φυλακες) which abolished riches, there is a class of private producers (δημιουργοι) be they rich or poor.
A number of provisions aim to avoid making the people weak: the substitution of a universal educational system for men and women instead of debilitating music, poetry and theatre. These provisions apply to all classes, and the restrictions placed on the philosopher-kings chosen from the warrior class and the warriors are much more severe than those placed on the producers, because the rulers must be kept away from any source of corruption. This warrior ruled society was based on the ancient Greek society in Sparta. The abolishment of riches among the guardian class leads controversially to the abandonment of the typical family, and as such no child may know his or her parents and the parents may not know their own children. The rulers assemble couples for reproduction, based on breeding criteria. Thus, stable population is achieved through eugenics and social cohesion is projected to be high because familial links are extended towards everyone in the City. Also the education of the youth is such that they are taught of only works of writing that encourage them to improve themselves for the state’s good.
Does the above sound familiar? Have you read Orwell? If not then I encourage you to spend some time with him. He is a good read.
Civil Rights?
It would be interesting to collect some statistics and identify how many people in the street actually know their civil rights. I guesstimate the following answers:
Freedom of speech
Freedom of information
Freedom of being
Freedom to act
Well, according to Socrates, we have to relinquish the above in order to achieve the perfect, just and secure society. Can you imagine that? Can you imagine a society where everything is centrally controlled, where no one is allowed to know how things are controlled, and where no one is allowed to think outside of the box without permission? Hang on…
Information Security is about Confidentiality, Integrity, and Availability of assets… of the society… of ourselves… Based on Plato, do we have to relinquish the CIA of “us” in order to achieve the perfect secure and just cyber-society? What is the cause of most cyber-crime? Power? Vengeance? Recognition? Money?
“A monetary system developed years ago as a device to control human behavior in an environment with limited resources. Today money is used to regulate the economy not for the benefit of the general populace, but for those who control the financial wealth of nations.”
Summary
After writing this document I think I am more confused than before. So, is hacking a criminal activity or not? Is knowledge a bad think or not? Is knowing what happens in society and having a critical opinion about it a bad thing or not? Is our place in life to simply accept what we will be fed without expressing a preference and/or an opinion? Do I have to relinquish my freedoms in order to be part of a society?
I was raised to believe that my liberties stop where the liberties of my neighbour start. I was raised to believe that I can do whatever I want as long as I do not annoy my neighbour. The laws of the land were not put together by my neighbour. The laws of the land were put together by a few, in order to support their interests, not my interests and certainly not the interests of my neighbour.
Why should we even care if an activity that we want to perform is criminal or not? The majority of the laws are not in the interest of the society anyway… Would it not be a lot better if we would be more concerned as to if the activity that we want to perform is just or not? Would it not be a lot better if we would be more concerned as to if the activity that we want to perform is ethical or not?
The fact is that ethics are a very expensive commodity nowadays and as we are in the business of making money no one wants to be ethical unless money can be made out of it. Nothing is ethical, everything is a façade, so why should I even discuss ethical hacking? The simple notion of it is a joke. Is it?
References & Bibliography (no time to do this properly… academics…)
AINSWORTH, P. 2001. Offender Profiling and Crime Analysis. Devon: Willan Publishing.
ALISON, L. 2005. The Forensic Psychologist’s Casebook: Psychological Profiling and Criminal
Investigation. Devon: Willan Publishing.
NYKODYM, N. TAYLOR, R. VILELA, J. 2005. Criminal Profiling and Insider Cyber Crime. Digital Investigation. 2 (4). Pp 261-267.
ROGERS. M. 2003. The Role of Criminal Profiling in the Computer Forensics
Process. http://www.2.tech.purdue.edu/cit/Courses/cit566/readings/Profile-Rogers.pdf (14th Jan 2010)
WILLIAMS, F (111). McSHANE, M. 2004. Criminological Theory. 4th Edition. New Jersey: Pearson Education
Kramer, R. (1985). “Defining the Concept of Crime: a Humanistic Perspective”. Journal of Sociology and Social Welfare, 5:469-487.
Snider, Laureen. (1993). “Theory and Politics in the Control of Corporate Crime” in Global Crime Connections: Dynamics and Control, (eds. F. Pearce and M. Woodiwiss). London: Macmillan, and Toronto: University of Toronto Press (pp212-40).
Hester, S., Eglin, P. 1992, A Sociology of Crime, London, Routledge.
Snider, Laureen. (2003). “Researching Corporate Crime” in Unmasking Crimes of the Powerful: Scrutinizing States and Corporations, (eds. S. Tombs and D. Whyte). London: Peter Lang (pp49-69).
Vidalis S. and Jones A., 2005, Analyzing Threat Agents & Their Attributes, in Proceedings of the 5th European Conference on i-Warfare and Security
Vidalis S., Jones A. and Blyth A., 2004, Assessing cyber-threats in the information environment, Network Security, Volume 2004, Issue 11, Pages 10 – 16
Stephenson, P., 2002, Collecting Evidence of a Computer Crime, Computer Fraud & Security, Volume 2002, Issue 11, Pages 17-19
Palmer G.L., 2002, Forensic Analysis in the Digital World, International Journal of Digital Evidence (IJDE), Volume 1, Issue 1
Jones A., 2002, Protecting the Critical National Infrastructure – Developing a Method for the Measurement of Threat Agents in an Information Environment Information Security Technical Report, Vol 7, No. 2, p.22-36
Casey, E., 2003, Determining Intent — Opportunistic vs Targeted Attacks, Computer Fraud & Security, Volume 2003, Issue 4, pp. 8-11
Leave a comment